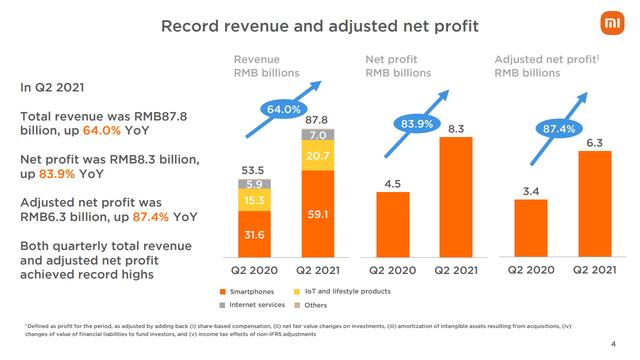
The image that "Mac OS is safer than Windows" is deeply rooted, and Apple itself appeals the safety of the OS itself with antivirus functions on its official website However, in response to the hit of Apple's products such as the iPhone, the ultra-thin "MacBook air" equipped with Mac OS is expanding its market share, and "PCs were infected with viruses" Viruses that display a message such as this and encourage the purchase of fake security software, and then disappear if the user pays the price, are spreading from malicious links posted on SNS such as emails and Twitter. There is a status quo. At that time, "ESET Cybersecurity", a Japanese version for Mac of "ESET", which has received a stable evaluation as a security software for Windows, has appeared, and a "free monitor version" that can be used until the end of October. is available for download, so I actually installed it and tried using it. ESET Cybersecurity
The conditions for installing "ESET Cybersecurity" are as follows. It supports Mac OS X 10.5 or later, that is, "Leopard" and "Snow Leopard", and plans to support the latest version of "Lion" at a later date. Although sales for overseas have already been done, this is the first time that a general version localized in Japanese has appeared. System requirements CPU: MacOS with Intel processor 32bit or 64bit: Mac OS X v10.5.6 Leopard or later or v10.6 Snow Leopard (planned to support Lion) Memory: 512MB Free disk space: 100MB Others: Internet connection environment, email address (Mobile address etc. are not allowed) First, double-click the downloaded "eset_cybersecurity_ja.dmg"
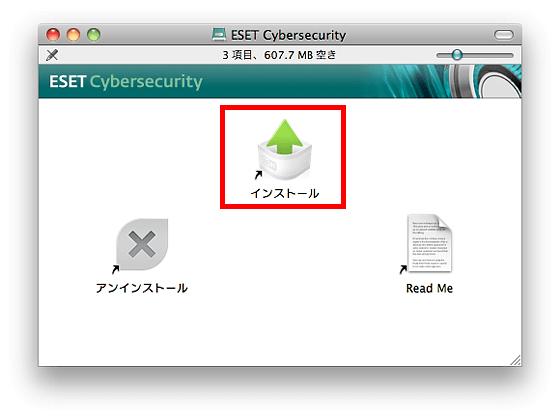
When this window opens, click "Install"
Click "Continue"
Click "Continue"
Click "Continue" again
Since the license agreement is displayed, read it and click "Continue"
An alert will appear asking if you agree to the license agreement, so click "Agree".
After confirming that "General (recommended optimal settings)" in the installation mode is checked, click "Continue"
The user name and password for the update server have already been entered, so click "Continue".
Make sure that Enable "ThreatSense.Net Early Warning System" is checked and click "Continue"
If you want to prevent an application from affecting your operation, you can select "Enable detection of unwanted applications" as an option, and the application will also be detected. Conversely, if you do not want to receive warnings from security software each time you install free software, "Disable detection of unwanted applications" is appropriate. Select whichever suits your usage and click "Continue".
You will be prompted to select an installation destination, but in this case there is no option other than "Macintosh HD" on the internal HDD, so click "Continue" without doing anything.
Click "Install"
Enter your PC user name and password and click "OK"
You will get an alert that you need to restart after installation, so click "Continue installation"
Installation will begin immediately.
The installation will finish immediately and you will be taken to this window. Click "Restart" to restart your PC and you're done.
When you restart, a splash like this will be displayed, and the update of the virus definition file will start automatically, so you can use the latest definition file distributed at the time of installation from the beginning. .
At this point, the software is resident, so first try downloading the test file from "eicar", which is famous as a test file for security software, and see if it can be detected. . This is a string "eicar.com" with a ".com" extension, which was detected and deleted the moment it was downloaded. Even when this warning window is displayed, there is no sound effect, and the window appears at the top right of the display and disappears after a few seconds, and there is no effect on other software operations.
The extension of "eicar.com" is changed to "txt", and the content is the same. The security software identifies double extensions and tries to find out files with extensions other than executable files such as .exe, and this was also detected firmly.
Since "eicar_com.zip", which is "eicar.com" compressed in ZIP format, was also detected, it can be seen that compressed files such as zip files are also subject to detection.
"eicarcom2.zip" is ZIP-compressed version of "eicar_com.zip". I can see if it can detect even double-compressed files, but I also detected it.
Since the green icon of "ESET Cybersecurity" is resident on the toolbar, click here and select "Show ESET Cybersecurity" from the displayed menu.
By default, it has a minimum menu structure called "Standard Mode", and basically it will stay resident and automatically remove viruses without any special settings, but here Click "Enable Advanced Mode" at the bottom left of the window to see all advanced settings, and explore each feature in advanced mode.
◆Protection statusLook at the menu on the left side of the window from top to bottom. Click "Protection status" to view the current security status. If you do nothing, it defaults to "Highest Protection".
If you select "Statistics" from the menu displayed directly below when you open "Protection Status", you can display a pie chart showing the statistics of infected files so far.
◆Computer Inspection Let's test the power of computer inspection. Click "Smart Inspection" to inspect the local disk.
Click to start inspection immediately.
Computer inspection completed in 1:24:39. It says "Number of infected objects: 3", but when I checked it using the log, I found that the eicar test file that was quarantined earlier was re-detected, and no threats that adversely affected the PC were detected. did not.
"Smart scan" scans all local disks, but if you want to narrow down the scope and scan only specific files, click "Custom scan". Then the setting screen opens, so you can set up the part you want to search.
◆UpdateSince it was automatically updated during installation, it says "Virus signature database is up to date".
◆SettingsChoose "Settings" and select "Antivirus and antispyware" to configure the state of protection that ESET Cybersecurity provides for your PC. Basically it is OK if you enable it, but if you want to stop protection once for some reason, click "Disable" in the center part of the window.
You can configure Real-Time File System Protection by clicking the "Configuring" link in the middle of the window. "Inspection time" is checked by default. For more detailed settings, click the "Settings" button in "ThreatSense Engine".
This will open an additional window. "Inspection target" is basically set only for files.
In "Options", you can adjust how much special applications are detected when inspecting.
Cleaning allows you to adjust the level of cleaning. The default is intermediate, but you can choose to treat infected files more aggressively and choose "Strict cleaning" or "No cleaning".
You can turn on/off "SMART optimization" in "Others". However, unless you want to run only user-configured scans, this feature will optimize settings with each update to ensure the most efficient scan level while keeping the speed of the scan at its best. , the scan will be more comfortable if left on.
Let's take a look at the settings other than "Antivirus/Spyware". The ID and password automatically entered at the time of installation are already entered in "Enter user name and password for updating" at the top.
If you select "Set a proxy server", the setting screen will be displayed.
"Import/Export Settings" allows you to export your own settings or import a setting file you have on hand, which is convenient when carrying over settings to the next generation machine.
If you want to reset various individual settings to the default, select "Reset all settings to default" and click "OK" in the pop-up window to initialize.
If you click "Enter application settings", you will jump to the proxy server setting screen, but if you select "Media" on the upper tab, you will be set to block all removable media such as CD-ROM and USB. You can also However, I don't think there are many people who don't use USB or CD-ROM at all, so this setting is for use in special environments where confidential information is handled.
◆Tools Tools allows you to view logs, quarantine infected files, and schedule scans.
The log file contains "threats detected", "events" that can be set by the scheduler described later, and logs when "computer inspection" is performed, and can be viewed.
The Quarantine records the date and type of files detected as threats and how they were dealt with. Even if it is detected as a threat by mistake, you can restore it by pressing "Restore".
In "Scheduler", you can set commands to be executed automatically when the software starts. This is the default setting.
You can also create new tasks. There are five types of tasks that can be set: ``Run applications'', ``Updates'', ``Log maintenance'', ``Computer inspection'', and ``Check system startup files''.
The Mac version "ESET Cybersecurity" has the same capabilities as the Windows version software, and if it is connected to the Internet, it will automatically update the definition file and monitor all downloaded files. . Although it was possible to use sufficient protection functions even when it was installed, it was a product that could be further customized with optional settings according to the user. Since it can be used free of charge until October 31, 2011, Mac users who have not installed any security software at present may download it from the following site and try it. ESET Cybersecurity
Copy the title and URL of this article・Related content
in Software, Advertising, Posted by darkhorse_log
You can read the machine translated English article here.