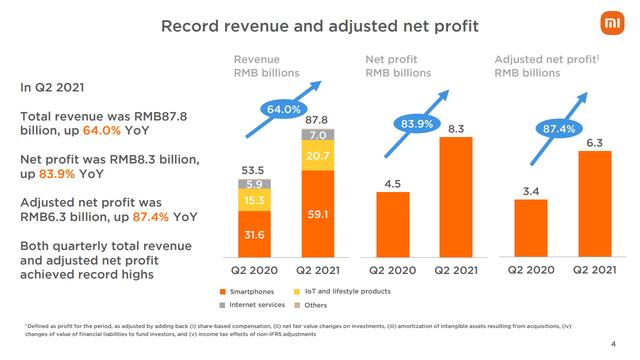
It's terrible, but this is the real thing now.
Black Lives Matter's protests are continuing around the world, triggered by George Floyd's death. Many of them are peaceful, but it is said that US law enforcement agencies are still tracking the movements of demonstrators through smartphone data and other means.
In fact, the data of our smartphones and internet usage is flowing not only to the police but also to various places without our consciousness. Reporter Shoshana Wodinsky of Gizmodo in the United States has summarized how to grasp the flow of such data and stop it in a hurry.
I think it can't be helped if everyone feels helpless now. In every city in the United States, demonstrators on the waist have been violent by police officers, who are protected by the US legal system and support from the Trump administration.
The US Congress is arguing whether it's a good idea to treat Lynch as a hate crime in this era of 2020. On the other hand, the pandemic of the new coronavirus is not over yet. As such, even if you are a person who has not been victimized by police violence, has not been affected by corona, and is superficially unharmed, your privacy is threatened more than you can imagine on the digital side.
But when it comes to privacy, there are things you can do without having to stretch yourself. However, it is not always easy.
Ironically, the more you know about digital privacy, the deeper you will feel helpless. It is said that the privacy protection law that protects us from data collection technology has been passed, but a little research reveals that it is not protected. It is said that if you wear a mask, your face will not be recognized, but a little research reveals that this is not the case. A little more research reveals that the "privacy protection" gold medal that all major tech companies sing is full of tatemae.
The other day, when I wrote an article about how smartphones are being tracked by the police, a myriad of questions came from people in the activist community who wanted to get rid of it. But for me personally, something close to guilt has come up.
The Electronic Frontier Foundation calls it "surveillance self-defense" and it is really amazing to put together various thorough guides for self-defense of privacy, but after all, such guides and various researches are companies and people who make various apps and sites. Is based on the assumption that is not lying. That's why many companies share it out of sight, saying, "We don't'sell'the data." They are hawking when we can't prove their lies. And in many cases, unfortunately, that's right.
Companies like Facebook and Google may not be loyal (or honest) to us, but we must be honest with our business partners. The partner companies are millions of advertisers, hundreds of ad tech partners, and imaginary investors and venture capitals who squeeze cash on the other side.
The best way for us to protect digital privacy is to think the same way they think companies do. In other words, think of it as a business. I can't write articles like "10 Recommended Apps for Activists" with confidence, but I can summarize the tips on what it means to use the internet carefully. So, below, I will tell you that as an answer to the three frequently asked questions.
"If you use a browser like VPN or Tor, will it disappear from the police?"
Everyone may or may not use both VPN and Tor, depending on what they want to do with their privacy.
If you don't want to get caught up in targeted advertising technology, a browser like Firefox can help you do something you can't do in Chrome's secret mode. With a VPN, you can hide web usage logs that may be sold to your ISP, and block advertisers (or authorities) who try to abuse your IP address.
However, VPN is a problem because there is no regulation in VPN, and there are not cases where the VPN operator himself sold the data once or twice, so check the identity of the operator in advance. Makes sense (the VPN illusion is organized here).

Tor may be the best way to make it harder to track, but Tor also has some problems. First of all, the mechanism used by Tor's backend to hide a user's identity is very powerful, but it makes the browser very slow and difficult to use. Ironically, because you're using a super-secure browser, the authorities can flag you as a suspicious person.
The Intercept also has a polite guide to protecting your privacy, which I highly recommend. That's because some of the tools they're talking about protect you from both malicious people and advertisers, two birds with one stone.
But if you can't believe such a privacy protection tool, you'll also find ways to monitor potentially leaked data.
"I'm using an app or site for protests, but I'm worried about where the data goes. Is there a way to check it myself?"
A tool for this very purpose, for example, is Wireshark, which Gizmodo has covered in the past. But using Wireshark or Charles Proxy, a traffic monitoring tool, requires some coding know-how.
I personally use Charles Proxy to track the data that third parties are pulling from my phone. For those who want to know more about this, there is also a very good guide that explains from a beginner's point of view.
There is a way to monitor monitoring, even for those who find programming annoying. For example, Built With allows you to break down trackers hidden in your website, and tools such as Ghostery and Privacy Badger can block monitoring.
It's a little difficult to look up smartphone data without coding skills, but it's not impossible. On iOS, it's easier to check the permissions that the app requires, and on Android, the permissions that the app pulls can be freely checked with online tools created by people in the Android community, or you can check it yourself. ..
On both iOS and Android, you can use paid services such as App Figures and App Annie to check if your app has third-party ad tech software that sucks data.
"Personal information" has many meanings, but I always think of the most disappointing layer cake in the world. On one side is our smartphone and on the other side is the data broker. Each third party may seem harmless at first glance, but as you dig deeper, it's more than just an app or site snooping on your location, and that data is taken by the police (or other). You may see a ugly company that you are giving to someone).
Use tools like the ones above to make sure your data is passed on to someone else (not just one, maybe 10 or 20), depending on the app. You may be able to. At that time, some may feel anger or despair, or rather a dark relief that their paranoia was right. Just this is good! The worst thing about it is that I'm doing this work properly.
"I found out that an app / site is sending my data to Facebook / Google / uncle relatives, etc. What does that mean?"
Again, on a case-by-case basis, it depends on what apps and sites are doing it, what data is being sent, and to whom you don't want to pass the data. It takes hours (maybe days) to analyze this kind of thing, and that's why such a suspicious service can be news in itself.
Ultimately, the reason major tech companies and non-major companies use third-party trackers is that they're easy for developers to put on and understand. If a developer can see the data sent by a tracker, that means anyone can see it.
For example, Zoom may not say what data it is extracting from the user's call and passing it to the FBI, but the data it shares with the Facebook is in a pre-determined box in the software code. Must be. In order for Zoom, or any app that shares data with Facebook, to share data with Facebook, you have to clearly define the data to be passed.
And while that definition might say something like "every time a user opens an app" or "when an ad clicks", it shouldn't include eavesdropping on Zoom calls. How we define "data" is very important.
According to a 2019 American Press Institute survey, nearly three-quarters of Americans agreed on the importance of reporters to monitor power. I am one of the majority. But when the abuse of power progresses systematically like it does now, it's more troublesome than when it happens suddenly. Even if you accuse police of racism, it's easier to say when it's obvious. Similarly, it's easy to accuse a tech company when you're handing over your data to the Immigration and Customs Enforcement Authority (ICE), but it's harder to pursue quiet and slow-moving wrongdoing. ..
In terms of human rights and digital privacy, corruption is calling for corruption, and many people need to act in their own way to turn the tide.
The way to combat organized racism may be to donate to a sympathetic group or to participate in a demonstration in the city. And protecting your online life means outsmarting your app.
Source: New Republic, Economist, The Root, Electronic Frontier Foundation (1, 2), The Guardian, Ars Technica, Statista, Facebook (1, 2, 3), Mozilla, Threat Post, Lifehacker (1, 2, 3), DBS, BuzzFeed, The Intercept, Charles Proxy, Knight Lab, Built With, Ghostery, Privacy Badger, 9to5mac, AAPKS, SISIK, App Figures, App Annie, The Verge (1, 2), Fortune, Business Insider, American Press Institute, Vox, THE CITY, Washington Post